Key insights
- If your e-signature workflow includes PHI, your vendor is a business associate and must sign a Business Associate Agreement (BAA).
- Regulators continue to penalize inadequate security risk analysis—a common gap uncovered during investigations.
- Big breaches remain a reality; highly connected vendors can amplify risk without strong identity, logging, and encryption controls.
- ESIGN/UETA make eSignatures legally valid, but HIPAA adds the security and privacy guardrails—both are required.
- SignNow’s HIPAA-ready capabilities (BAA on eligible plans, encryption, audit trails, MFA, transparent pricing) give SMB and mid-market teams a secure, scalable path forward.
What is an electronic signature in healthcare?
Electronic signatures are legally recognized in the United States thanks to the federal ESIGN Act and state-level UETA laws. But legality is just the starting point in healthcare. If PHI is part of the eSignature workflow, HIPAA’s Privacy and Security Rules come into play.
HIPAA treats electronic signature software for healthcare providers, health plans, and their vendors as business associates. Under federal regulations, any company with routine access to PHI must sign a Business Associate Agreement (BAA) and follow strict rules on privacy and security. Business associates are directly liable for certain violations, meaning the stakes are high for everyone involved.
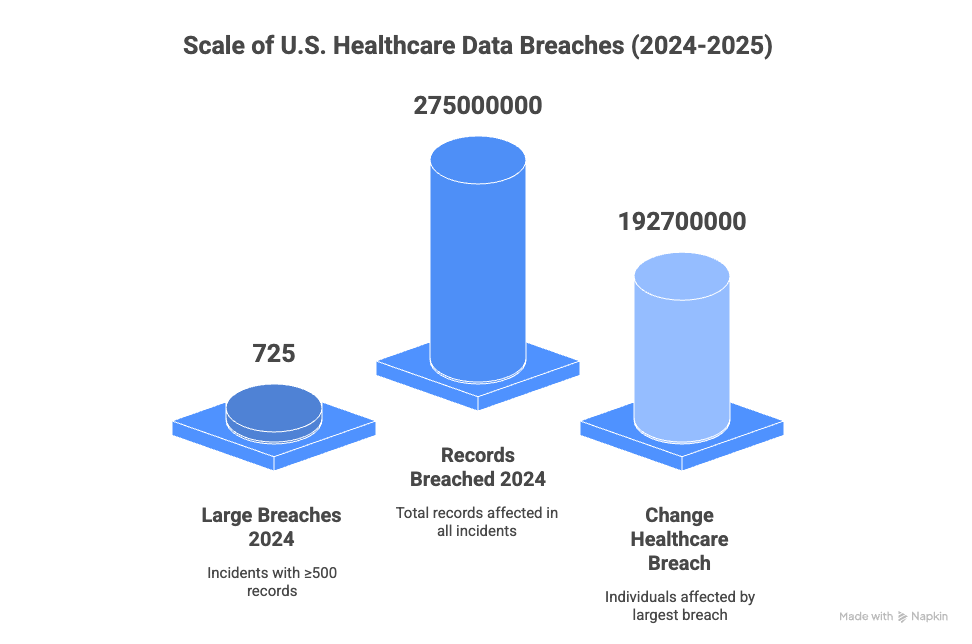
Recent trends highlight why these safeguards matter. In 2024, the U.S. Department of Health and Human Services received reports of 725 large healthcare data breaches—each involving at least 500 patient records. The largest, the Change Healthcare breach, ultimately affected approximately 192.7 million individuals, making it the biggest health data exposure on record (HIPAA Journal, Reuters). The 2024 IBM Security Cost of a Data Breach Report found that healthcare remains the most expensive industry for data breaches, averaging $9.77 million per incident. Breaches lasting over 200 days cost about $5.46 million, and credential-based attacks were both widespread and slow to contain, often exceeding 290 days in duration.
Regulatory enforcement is also on the rise. The Office for Civil Rights (OCR) reported a cumulative 152 cases with roughly $144.9 million in settlements and penalties to date, with risk analysis failures and insufficient safeguards often at the center of these actions.
Against this backdrop, essential capabilities like robust access controls, exportable audit logs, reliable encryption, and a solid BAA are non-negotiable. These features form the foundation of any eSignature platform serving healthcare providers, health plans, or business associates—and help reduce the risk of breaches and regulatory action.
What a “HIPAA-Ready” electronic signature looks like
Choosing a compliant eSignature solution requires looking beyond the basic features. Here are the key elements that demonstrate a vendor is prepared to handle PHI safely.
Signed and specific business associate agreement (BAA)
A BAA is more than a checkbox; it’s a critical legal contract. It must clearly define timelines for breach reporting, outline how information can be used, detail responsibilities for subcontractors, and establish a shared security model. When evaluating vendors, ask for a sample BAA to review their terms.
Support for your risk analysis
Your security risk analysis (SRA) is a cornerstone of HIPAA compliance. A vendor should provide data-flow diagrams, control mappings, and logging evidence to support this process. Your compliance team needs to be able to trace how PHI is collected, stored, sent, and deleted within the platform.
Strong identity and access controls
Protecting PHI starts with controlling who can access it. Look for features like multi-factor authentication (MFA) for senders and signers. The platform should also support role-based access control (RBAC) and single sign-on (SSO) to enforce least-privilege permissions. For patient-facing documents, consider ID verification options for higher-risk situations.
Detailed and immutable audit trails
Every action involving a document must be recorded in a permanent, timestamped log. This includes creation, viewing, sending, signing, downloading, and any administrative changes. You should be able to export these logs for audits or investigations without needing help from the vendor.
Data integrity and encryption
Ensure the platform uses hashing to protect document integrity, TLS encryption for data in transit, and strong encryption for data at rest, including backups. These protections must apply across all channels, including web, mobile, and API, as well as for any attachments.
Clear incident response and notifications
The vendor should have a documented incident response plan. Ask for evidence of security drills and clear communication protocols for breaches, as outlined in your BAA. You need to know who notifies whom, within what timeframe, and how remediation efforts are coordinated.
Alignment with security standards
A vendor’s alignment with frameworks like the NIST Cybersecurity Framework (CSF) and HHS 405(d) shows a commitment to recognized security practices. Request a control matrix that maps their features to specific HIPAA Security Rule citations, such as regulations on administrative security safeguards and technical requirements and §164.312.
How SignNow supports healthcare teams
The importance of robust compliance and security in electronic signature software for healthcare cannot be overstated, especially as the risk landscape grows more serious each year.
SignNow provides healthcare organizations with the tools to send and sign documents quickly, backed by safeguards designed for HIPAA-aligned workflows. Our platform is built to support the needs of small to mid-market providers and plans.
- BAA on eligible plans. SignNow executes a BAA with covered entities and their business associates, allowing you to route PHI with confidence.
- Essential security controls. SignNow includes encryption in transit and at rest, detailed audit trails, access controls, and two-factor authentication to support HIPAA’s technical safeguards.
- Transparent pricing. SignNow’s pricing is straightforward. You won’t find hidden support fees, surprise add-ons, or steep renewal increases, which helps you align with healthcare budgeting cycles.
- Flexible user access. Many of SignNow’s paid plans support broad user access, so you can expand the platform across departments and partners without worrying about seat licenses.
- 24/7 support. SignNow provides responsive assistance for your clinical, back-office, and revenue cycle teams whenever you need it.
Mapping SignNow to your HIPAA needs
| HIPAA requirement | How SignNow Addresses It |
| BAA required | We execute a BAA on eligible plans. |
| Audit controls | Full, exportable audit trails track every document action. |
| Access & authentication | We offer role-based controls, 2FA, and SSO options. |
| Integrity & encryption | Document integrity is protected; we use TLS and strong at-rest encryption. |
| Risk analysis support | We provide the artifacts and logs needed for your SRA and governance. |
Where compliant eSignatures make a difference
Implementing an electronic signature for healthcare streamlines critical processes while maintaining security.
- Patient intake and consent: Digitize consent forms, privacy acknowledgments, and pre-op approvals with a complete audit trail. Use MFA for staff and add verification steps for high-risk forms.
- Provider credentialing: Securely move credentialing packets and privilege forms between hospitals, staffing agencies, and payers. This confines PHI to protected workflows and helps get providers scheduled faster.
- Home health and telehealth: Route plan-of-care updates and durable medical equipment (DME) orders to remote teams and patients with the same security you have on-site. API integrations enable telehealth platforms to securely trigger signatures.
- Revenue cycle management: Shorten the revenue cycle by digitizing financial assistance applications and payer appeals. The platform’s logging and encryption will satisfy auditor requirements.
- Clinical research: For workflows involving regulated records, you can layer HIPAA safeguards with the documentation needed for research oversight, ensuring both speed and traceability.

Buyer’s checklist for healthcare eSignature software
Use this checklist to evaluate electronic signature software for healthcare providers and plans:
- Does the vendor willingly sign a BAA and provide a sample for review?
- Can they demonstrate MFA, role-based access controls, and exportable audit trails?
- Do they offer clear documentation on their encryption methods for data at rest and in transit?
- Can they provide artifacts to support your organization’s security risk analysis?
- Is their pricing for users, envelopes, and API calls transparent and predictable?
- Do they align their security practices with standards like NIST CSF and HHS 405(d)?
- How responsive is their support team when your daily operations are on the line?
If you are evaluating these items, SignNow was built to meet your requirements.
Implementation guide: From pilot to full scale
Follow these steps to successfully roll out an eSignature solution.
- Define scope and data flows. Start by listing the first forms you want to digitize, such as intake or consent forms. Map where PHI originates, where it is stored, and who interacts with it.
- Finalize the contract. Execute the Master Services Agreement (MSA) and the BAA. Ensure the terms for breach notification and subprocessor management align with your internal policies.
- Harden identity and access. Enable MFA for all users who send documents. Configure roles for clinicians, registrars, and financial staff to enforce the principle of least privilege.
- Configure auditing and retention. Set up immutable logs and configure retention policies that meet your legal and medical record requirements. Test log exports to ensure they work as expected.
- Build templates and guardrails. Create standardized templates for clinical and financial forms. Use features like required fields, signer routing, and expiration dates to minimize errors.
- Train staff and simulate incidents. Conduct training exercises for common scenarios, like a misaddressed document or a lost device. This validates your response plan and clarifies who is responsible for each step.
- Measure and expand. Track metrics like cycle time, completion rates, and staff effort saved. Use this data to justify expanding the solution from a pilot to a wider rollout.
Common pitfalls and how to avoid them
The risks of overlooking HIPAA requirements are real—and costly. In 2024 alone, there were 725 large healthcare data breaches reported to HHS, with the Change Healthcare incident exposing the records of nearly 192.7 million people. Breaches are not just more frequent; they are more expensive.

Enforcement is increasing as well—regulators have imposed over $144 million in settlements and penalties for HIPAA violations to date, with recent cases highlighting failures around security risk analysis and incident response.
That’s why addressing these common pitfalls is essential:
- Confusing “legally valid” with “HIPAA compliant”: The ESIGN Act makes eSignatures legal, but HIPAA governs PHI protection. You need both.
- Weak identity controls: Stolen credentials remain a top security threat. Enforce MFA across the board and monitor for unusual access patterns.
- Shadow IT and unapproved integrations: Forwarding emails or downloading documents to personal cloud storage can expose PHI. Standardize on approved integrations and export paths.
- Vague audit trails: If your logs can’t prove who did what and when, they won’t pass an audit. Validate the level of detail in your audit trails before going live.
Stale security risk analyses: An SRA is not a one-time task. Update it whenever you add new forms, departments, or integrations to your workflow.
Final thoughts
Expectations for identity management, logging, and encryption are continually rising due to new rules and market demands. The most secure path forward is to choose an electronic signature platform that treats HIPAA readiness as a core product feature.
With SignNow, you get a solution that provides:
- Compliance-ready features out of the box.
- Predictable pricing that scales with your needs.
- A dedicated partner offering 24/7 support.
Elevate your critical workflows. Start your free SignNow trial today!
Glossary
- Business Associate Agreement (BAA): A legal contract that ensures a third-party service provider protects patient health information when working with healthcare organizations.
- Electronic Signature (e-signature): A digital way to sign documents that verifies a person’s identity and secures the document.
- HIPAA (Health Insurance Portability and Accountability Act): A U.S. law that sets rules to keep patient health information private and secure.
- Protected Health Information (PHI): Any personal health details that can identify a patient and must be kept confidential under HIPAA.
FAQ
1. Do I need a Business Associate Agreement (BAA) with my electronic signature provider?
Yes. Under HIPAA, if your eSignature vendor can access protected health information (PHI), they are considered a business associate. You must have a BAA in place before using the software for any documents containing PHI.
2. What security measures should electronic signature software for healthcare include?
Look for solutions with multi-factor authentication (MFA), strong encryption (in transit and at rest), detailed audit trails, and robust access controls. These measures are required to meet HIPAA’s technical and administrative safeguards and reduce your risk in case of an audit or breach.
3. Are electronic signatures legally valid for healthcare documents in the U.S.?
Yes. The ESIGN Act and UETA make electronic signatures legally valid nationwide, but HIPAA requirements still apply if PHI is involved. Legal validity must be paired with HIPAA security and privacy protections.
4. How does a provider know if an eSignature platform is HIPAA compliant?
Check that the vendor signs a BAA, provides documentation of their security controls and risk analysis support. Compliance documentation and a willingness to demonstrate safeguards are good indicators.
5. What steps can I take to stay up to date with regulatory changes impacting eSignature healthcare providers?
Monitor updates from HHS, OCR, and industry resources about HIPAA changes and security regulations. Work with partners like SignNow who actively update their features in response to new laws and provide guidance to help you remain compliant.
- Key insights
- What is an electronic signature in healthcare?
- What a “HIPAA-Ready” electronic signature looks like
- How SignNow supports healthcare teams
- Where compliant eSignatures make a difference
- Buyer’s checklist for healthcare eSignature software
- Implementation guide: From pilot to full scale
- Common pitfalls and how to avoid them
- Final thoughts
- FAQ